Secret: First Step¶
Create a Secret¶
Secrets are deployed using manifest files through the Command Line Interface (CLI). During this deployment, Poros, the Resource Manager, orchestrates the forwarding of Secret Resource YAMLs to Heimdall, the Governance Engine within DataOS. To create a Secret Resource in DataOS, follow these steps. This guide assumes you have the necessary permissions and access to the DataOS CLI.
Create a manifest file¶
Begin by creating a manifest file that will hold the configuration details for your Secret.The structure of the Secret manifest file is provided in the image given below:
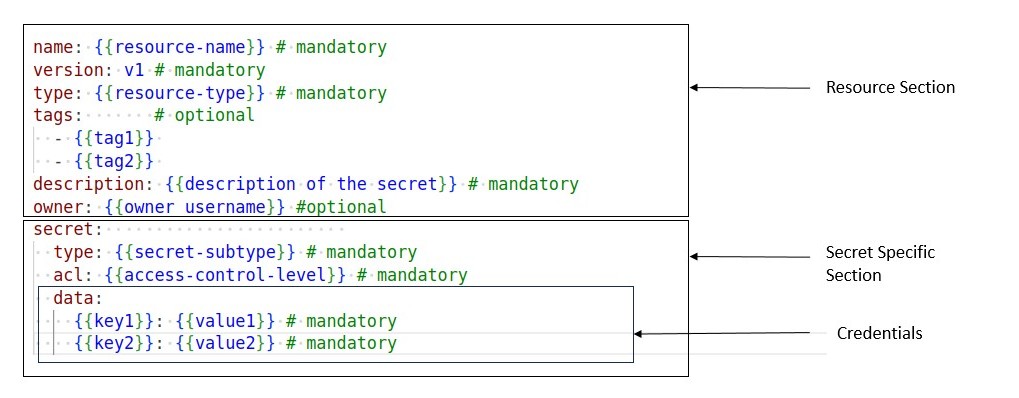 The manifest file of a Secret Resource can be broken down into two separate sections - Resource meta section and Secret-specific section.
The manifest file of a Secret Resource can be broken down into two separate sections - Resource meta section and Secret-specific section.
Resource meta section¶
The Resource meta section of the manifest configuration file encompasses attributes that maintain uniformity across all resource types. The provided manifest snippet illustrates the key-value pairs that must be declared in this section:
name: ${{resource-name}}
version: v1
type: ${{resource-type}}
tags:
- ${{tag1}}
- ${{tag2}}
description: ${{description of the secret}}
owner: ${{owner_username}}
Secret-specific section¶
The Secret-specific Section of the manifest configuration file includes key-value pairs specific to the type of Secret being created. The following manifest snippet illustrates the key values to be declared in this section:
Secret manifest Fields¶
The table below provides a summary of the various attributes of the Secret-specific section:
| Field | Data Type | Default Value | Possible Value | Requirement |
|---|---|---|---|---|
secret |
object | none | none | mandatory |
type |
string | none | cloud-kernel, cloud-kernel-image-pull, key-value, key-value-properties, certificates | mandatory |
acl |
string | none | r, rw | mandatory |
data |
mapping | none | none | mandatory |
files |
string | none | file-path | optional |
For more information about the various attributes in Secret specific section, refer to the Attributes of Secret specific section.
Apply the manifest¶
To apply the Secret manifest, utilize the DataOS CLI by explicitly specifying the path to the manifest file and the designated workspace. The apply command is provided below:
Warning
If the connection credentials contain special characters such as @ : / ? # & = + ; % \ ' { } ( ) * $ !, the --disable-interpolation flag must be used when applying instance-secrets or secrets. This ensures that special characters are retained as-is in the string.
Example:
Alternative to the above apply command.
Manage a Secret¶
Validate the Secret¶
To validate the proper creation of the Secret Resource within the DataOS environment, employ the get command. Execute the following command to ascertain the existence and correctness of the Secret Resource:
Alternative command:
Delete the Secret¶
To remove the Secret Resource from the DataOS environment, utilize the delete command within the CLI. Execute the following command to initiate the deletion process:
delete command structure for -t (type) and -n (name)
Alternative command:
delete command structure for -i (identifier)